 This is a guest post by Joe from New Customer Workshop. The New Customer Workshop helps local business owners master internet marketing in order to increase traffic into their stores.
This is a guest post by Joe from New Customer Workshop. The New Customer Workshop helps local business owners master internet marketing in order to increase traffic into their stores.
Introduction
Over at the New Customer Workshop I talk a lot about how you can use Twitter to promote your local business and build a community of passionate customers.
Recently, I’ve noticed an increase in the amount of spam coming from businesses I follow on Twitter. The spam looks something like this:
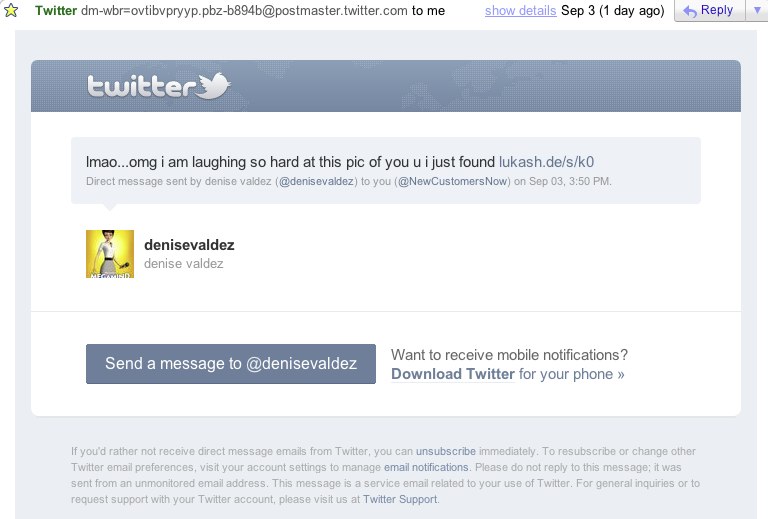
Instead of showing me a funny photo of myself the link will drop me on a website that tries to steal my Twitter account information.
These Tweets clearly weren’t sent by the Twitter account holder. Rather, the account was likely phished and now someone is sending Tweets using the hacked account.
A hacked Twitter account is more than just an inconvenience.
It can harm your brand.
You should treat the safety of your Twitter account like you would your store or home. Make sure it’s locked up tight and don’t give the keys to strangers.
It’s simple to do if you follow a few best practices.
Don’t Give Strangers Access To Your Account
Twitter has a rich ecosystem of tools built for managing Twitter lists, auto-tweeting, measuring your influence and more.
The dark side of this is that some unscrupulous tool vendors will steal your account information and use it to send Twitter spam through your account.
Recently a tool claiming to track Twitter stalkers was released.
This “tool” is fake and is used to steal account information.
That doesn’t mean you shouldn’t check out some of these great tools. Just be smart about who gets access to your account information.
First, make sure that the tool you are using isn’t doing anything to violate Twitter’s terms of service.
If the tool promises to give you thousands of followers
it’s probably not safe to use.
Second, do some diligence on the tools. If you find one that looks interesting search for reviews on Growmap, Mashable or even just Google.
Finally, understand how the tools connect to your account. In order to work, most of these tools require some form of access to your Twitter account. This typically involves you granting permission through Twitter on behalf of the tool.

This is the preferred way to grant permissions. If a tool is requiring you to enter your username and password avoid it. Once someone has access to your username and password they can connect to your account and send Tweets masquerading as you.
Are You Really Using Twitter?
Another tactic used to gain access to your account is to send an official looking email to you asking you to take some action on your account. When you click the “Twitter” link you are directed to a page that looks like a Twitter login form. This was the tactic employed in the Introduction.
Make sure you are actually on Twitter.com
Not a site with a similar domain name
close enough you might not notice!Your account information is stolen when you
try to login through these fake forms.
You can protect your self by verifying that the URL of the Twitter page is actually twitter.com.

This video from Sophos shows how someone is tricked into giving their credentials to a fake Twitter website.
Be Smart About Your Passwords
It’s important to use a strong password on any account related to your business. It’s equally important that you use a unique password for each account you hold. That way if one account is compromised the others are still protected. The problem with that advice is it’s hard to remember a strong password, it’s even harder to remember it for each site you use.
There are a couple of ways to solve that problem:
- The folks over at Lifehacker have a great article on how you can create strong passwords that you easily remember or you can use GrowMap’s password convention.
- You can also use a program like 1Password to store all of your passwords. Then you only need to remember one master password. The password manager can fill out the login forms for the websites you visit.
I actually use both suggestions and feel pretty confident that my online identity is safe.
WHAT TO DO IF YOUR TWITTER ACCOUNT GETS HACKED
Help, I Was Hacked!
Despite your best efforts, you may still have your Twitter account hacked.
There are two things you need to do immediately if you think your account was hacked:
- Login in to Twitter and change you password. This will hopefully prevent future attacks through your account.
- Tweet a message to your followers to let them know what happened. Tell them to ignore any Direct Messages from you and to not click on any links.
Conclusion
Twitter is a great tool for communicating with your customers. Unfortunately, there are many people who try to steal your account information in order to spread spam. You can protect your brand identity on Twitter by following the best practices described here.
Do you follow any other best practices to protect your accounts? I’d love to hear about them in the comments.
If you want more great tips on using Twitter for marketing your local business follow @NewCustomersNow on Twitter or sign up for the free New Customer Workshop newsletter.
NOTE FROM GROWMAP: Urgent PRIVACY WARNING for Internet Users >>> HAVE YOU SEEN THIS YET? New forensics tool can expose all your online activity:
“We’ve built a tool that can reconstruct where the
user has been online, and what identity they used.”
The open-source software, Offline Windows Analysis and Data Extraction (OWADE), was launched at the Black Hat 2011 security conference and works with PCs running on the Windows operating system.
Making that public makes all of us more likely to be targeted by every digital thief in the world who will want to use it to steal credit card numbers and identities. I guess that shouldn’t surprise anyone since they launched it at a black hat conference.
There’s another good reason to use Linux. (I’m using Linux Mint and used Ubuntu for two years.) They may or may not get around to creating versions for Macs or Linux.
